Impose strong passwords with HashStrike
Unleash the beast with unique fusion of highly crafted software and hardware to audit and analyze passwords strength.

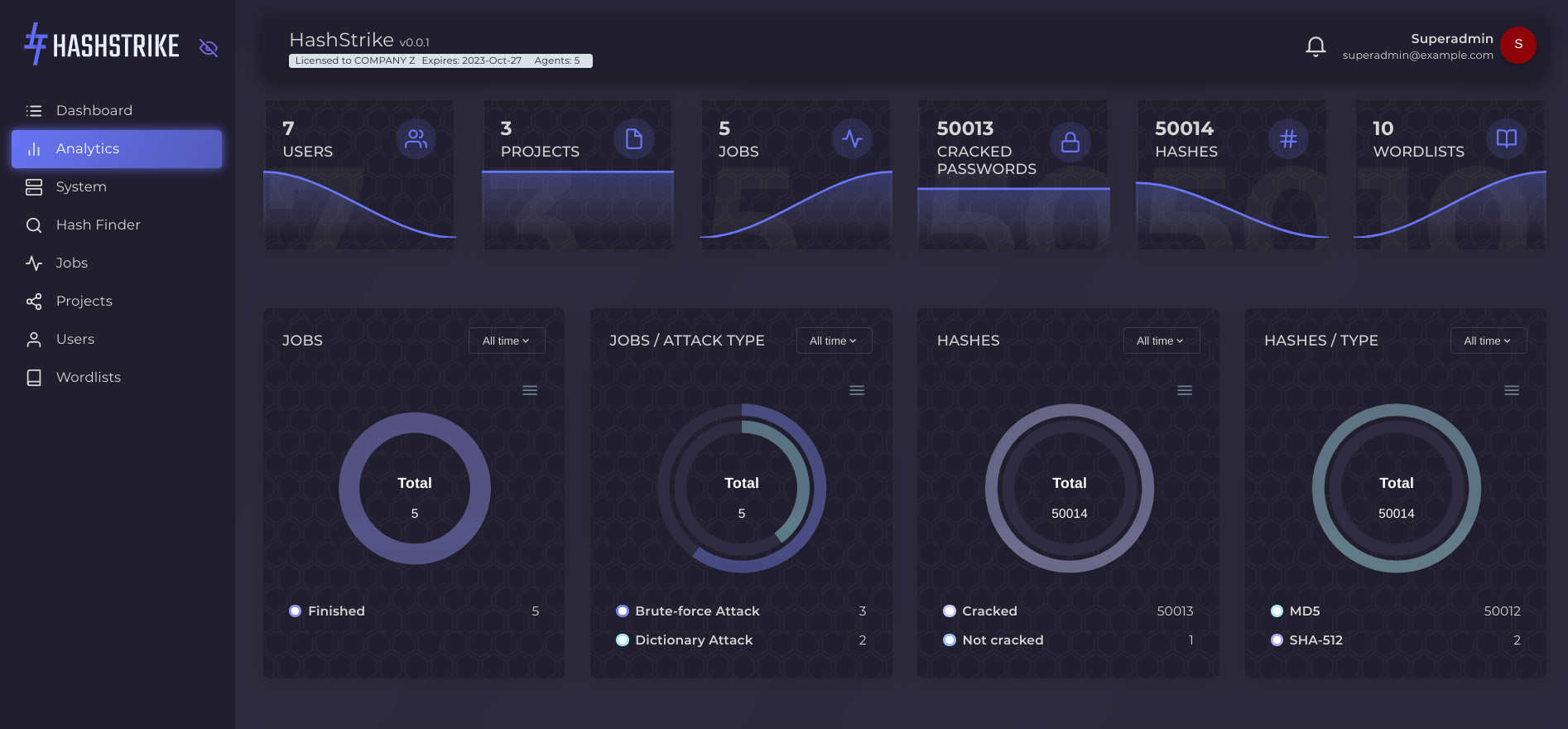
Deploy and integrate HashStrike seamlessly
Deploy
Start by deploying HashStrike controllers (agents) & dashboard (central server).
Connect
Connect GPU rigs to HashStrike agents and unleash the beast.
Unleash the beast
Audit passwords in terms of strength, complexity or even recover lost passwords.
Limit and minimize password related threats and incidents
Audit Password Strength
Verify and evaluate your organization’s passwords to meet password complexity requirements.
Wordlists & Hash Finder
Custom Wordlists that reflects common real-world passwords and innovative Hash Finder tool with advanced filtering capabilities.
Powerful Dashboard
Unique dashboard with interactive management interface to manage users, jobs, projects, agents and wordlists.
Distributed Workload
Accelerate your jobs by connecting multiple GPU Rigs with HashStrike agents seamlessly.
Multi Hash Support
HashStrike supports different hashing algorithms and password formats.
Collaberative Software
Initiate, share and collaborate projects with your team seamlessly.
Multiple bundles to suite your requirement
Software & Hardware
Software
Hardware
Software Only
Software
Hardware
Frequently asked questions
- What HashStrike is needed for?
HashStrike was designed to be used in different scenarios that include cybersecurity engagements, digital forensics and password auditing & recovery.
- Can I use multiple dictionaries with HashStrike?
- I have a half-known password, can HashStrike get the rest of the password?
- Does HashStrike utilize all the GPUs?
- What does HashStrike offer as a solution in terms of bundles?
- Can I have HashStrike as a PoC?
Limit password threats
Minimize your attack vectors by enhancing password complexity to its maximum. Audit employee passwords and meet compliance requirements with a user-friendly dashboard.
Contact Us